2021年6月8日,微软在6月的安全更新中通报并修复了一个Windows Print Spooler远程代码执行漏洞。6月29日,网络安全行业厂商发现该漏洞POC(概念验证代码)已在互联网公开,存在明显安全风险,提醒广大Microsoft师生用户尽快下载补丁更新,避免引发漏洞相关的网络安全事件。
微软官方补丁下载地址:https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-1675
漏洞概述:
Windows Print Spooler是Windows的打印机后台处理程序,广泛的应用于各种内网中,攻击者可以通过该漏洞绕过PfcAddPrinterDriver的安全验证,并在打印服务器中安装恶意的驱动程序。若攻击者所控制的用户在域中,则攻击者可以连接到DC中的Spooler服务,并利用该漏洞在DC中安装恶意的驱动程序,完整的控制整个域环境。
该漏洞广泛的存在于各Windows版本中,利用复杂度为中等,但由于成功利用该漏洞的攻击者可以完整的控制域环境,造成非常严重的后果,所以该漏洞的利用价值极高。
影响范围:
Windows Server 2019 (Server Core installation)
Windows Server 2019
Windows Server 2016 (Server Core installation)
Windows Server 2016
Windows Server 2012 R2 (Server Core installation)
Windows Server 2012 R2
Windows Server 2012 (Server Core installation)
Windows Server 2012
Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for x64-based Systems Service Pack 2
Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for 32-bit Systems Service Pack 2
Windows Server, version 2004 (Server Core installation)
Windows RT 8.1
Windows 8.1 for x64-based systems
Windows 8.1 for 32-bit systems
Windows 7 for x64-based Systems Service Pack 1
Windows 7 for 32-bit Systems Service Pack 1
Windows 10 Version 1607 for x64-based Systems
Windows 10 Version 1607 for 32-bit Systems
Windows 10 for x64-based Systems
Windows 10 for 32-bit Systems
Windows Server, version 20H2 (Server Core Installation)
Windows 10 Version 20H2 for ARM64-based Systems
Windows 10 Version 20H2 for 32-bit Systems
Windows 10 Version 20H2 for x64-based Systems
Windows 10 Version 2004 for x64-based Systems
Windows 10 Version 2004 for ARM64-based Systems
Windows 10 Version 2004 for 32-bit Systems
Windows 10 Version 21H1 for 32-bit Systems
Windows 10 Version 21H1 for ARM64-based Systems
Windows 10 Version 21H1 for x64-based Systems
Windows 10 Version 1909 for ARM64-based Systems
Windows 10 Version 1909 for x64-based Systems
Windows 10 Version 1909 for 32-bit Systems
Windows 10 Version 1809 for ARM64-based Systems
Windows 10 Version 1809 for x64-based Systems
Windows 10 Version 1809 for 32-bit Systems
通用修补建议:
目前微软官方已针对支持的系统版本发布了修复该漏洞的安全补丁,强烈建议受影响用户尽快安装补丁进行防护,官方补丁下载链接:https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-1675
临时修补建议:
若用户暂时无法进行补丁更新,可通过禁用Print Spooler服务来缓解漏洞风险。
1. 在服务应用(services.msc)中找到Print Spooler服务。
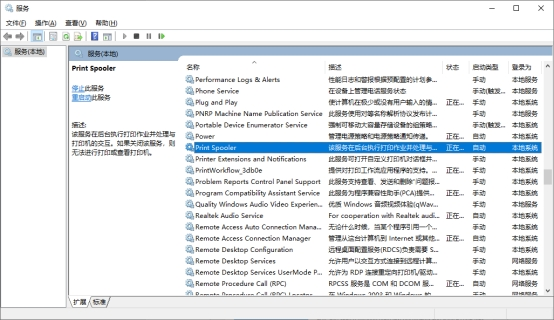
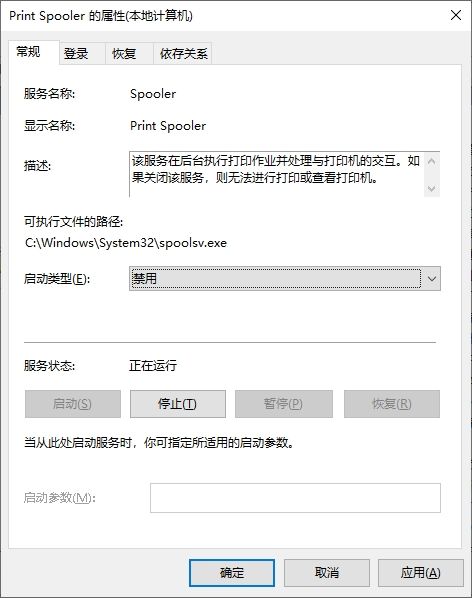
2. 停止运行服务,同时将“启动类型”修改为“禁用”。
信息化建设与网络安全办公室
2021年7月1日
参考链接:
https://cert.360.cn/warning/detail?id=e21e16d9547c441862910c7a05a5abb4



