A Tool Set for Role Mining
Welcome to RMiner
What Is RMiner?
RMiner provides user a visual role mining and role state updating platform. It provides the implementation of some classic role mining algorithms for generating roles and a role state editor for updating role state. In addition, RMiner offers some abstract interfaces that user can add new algrothims based on them. Users will easily discover a new algorithm's difference from others using the visualization tools. All these design of tool set are learned from WEKA.
The project includes seven algrothims currently:
ORCA
HierarchicalMiner
CompleteMiner
FastMiner
StateMiner
GraphOptimization
MinimalPerturbation
Who Uses RMiner?
The design of RMiner is according to the building process of an RBAC system. Users can use the platform to build an RABC system or do comparison experiments to analysis the difference between role mining algorithms. This platform is unified verification that simplifies the process of role mining research and experimental works.
Download
Please click here to download a release of RMiner.
Please click here to download all source code of RMiner.
Please click here to download a user's manual of RMiner.
All above resources can be downloaded from http://code.google.com/p/rminer.
Getting Started
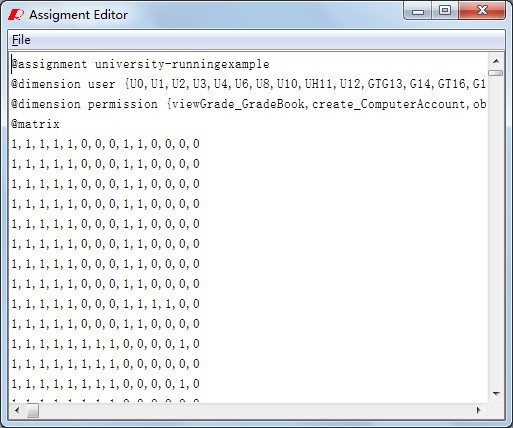
In order to maintain independence and generality of data set for role mining process, we develop the assignment relationship with attribute file format (TARF) based on attribute relation file format (ARFF) of WEKA. Therefore, you need to transform the other file format of user to permission relationship to TAFF format when starting.
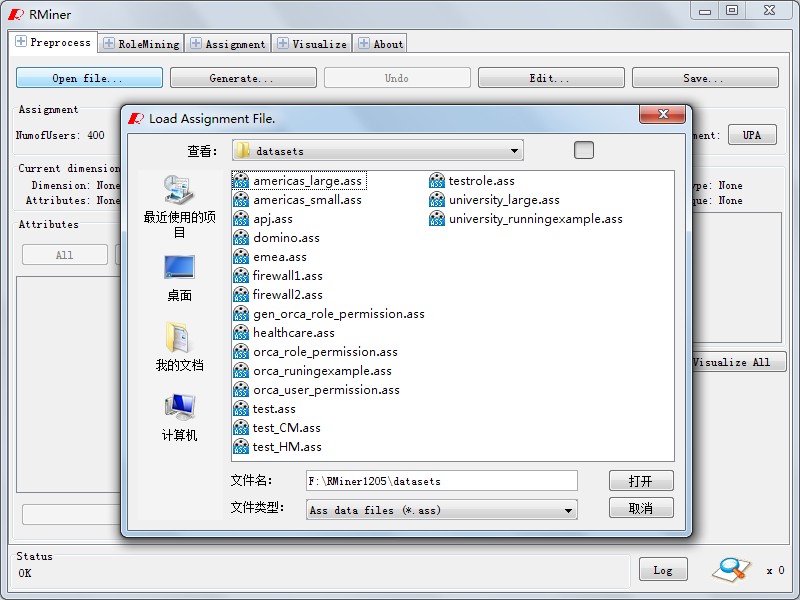
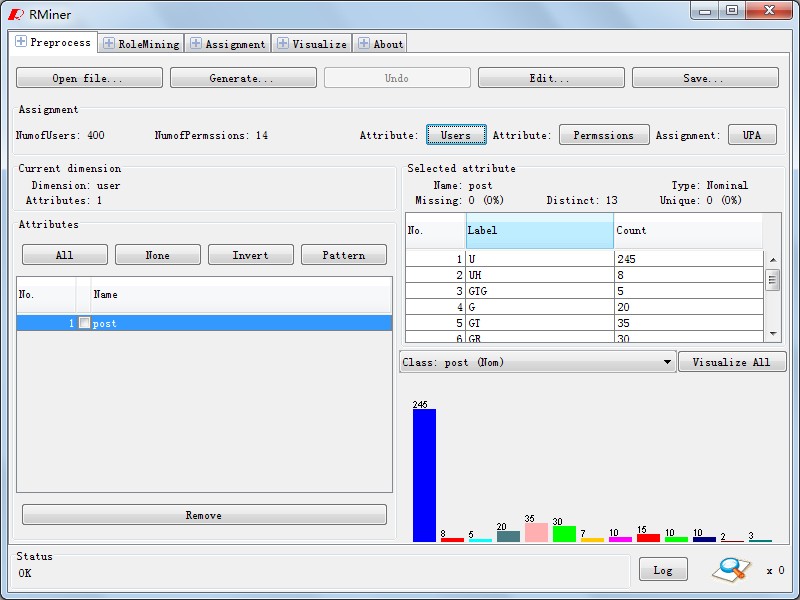
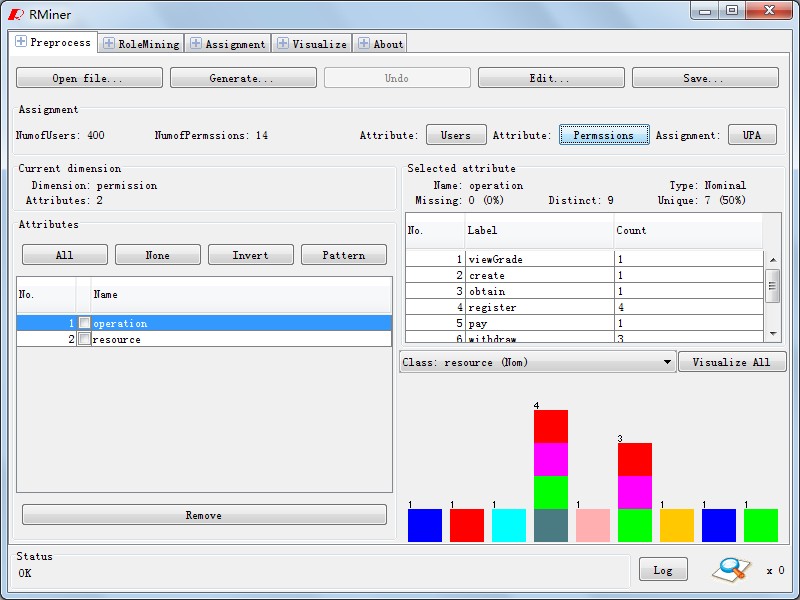
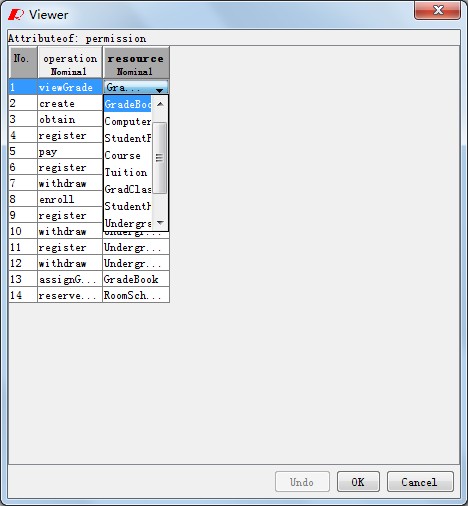
Fig1~5 is the preprocess of RMiner. Fig1 shows the data loading process. Button "Open File" helps you load the data. Fig2~4 show that you can statistics and modify the data after loading the data. Button "Users" analysises the distribution of attributes in the users as shown in Fig 2. Fig3 shows Permission-Attribute distribution which is called by the "Permissions" button. We also provide permission update fucntion for data modification, and employ button "UA" to do this as Fig4. Fig5 shows that you can modify the data accross"Edit" button.Of course , you should undermine the TARF format in new file.
|
Fig1. Data Loading |
Fig2. User-Attribute Statistics |
|
Fig3. Permission-Attribute Statistics |
Fig4. Permission Update |
|
Fig5. User-Permission Assign Update |
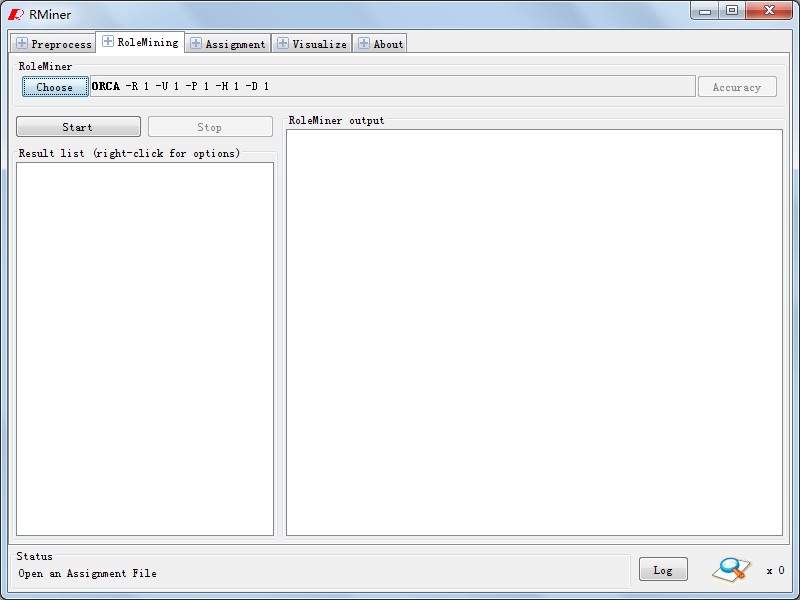
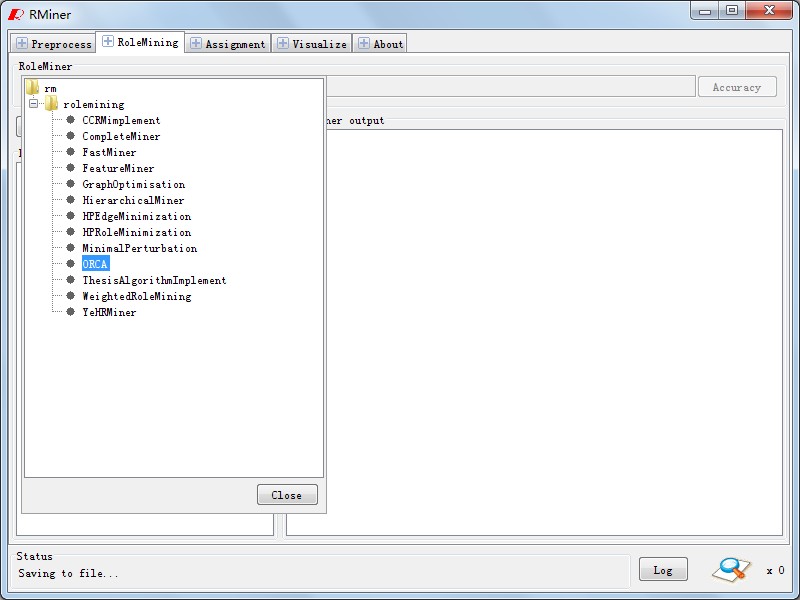
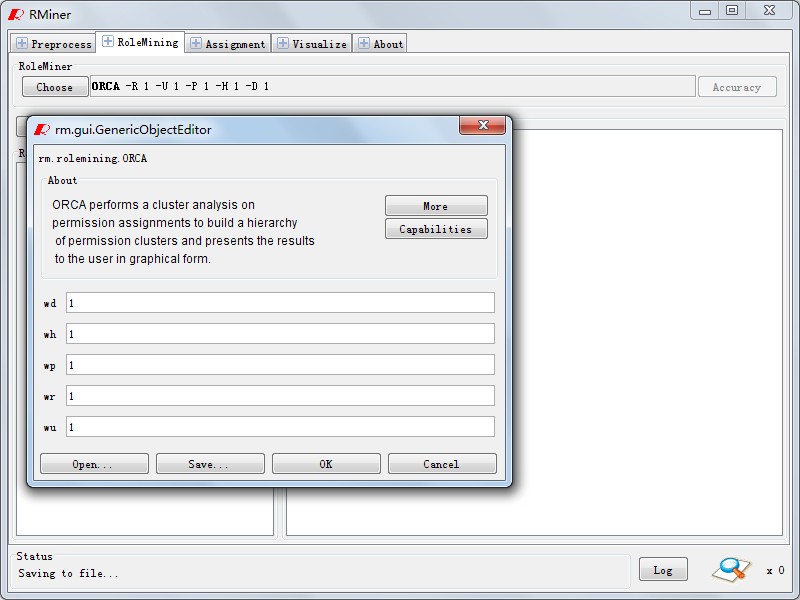
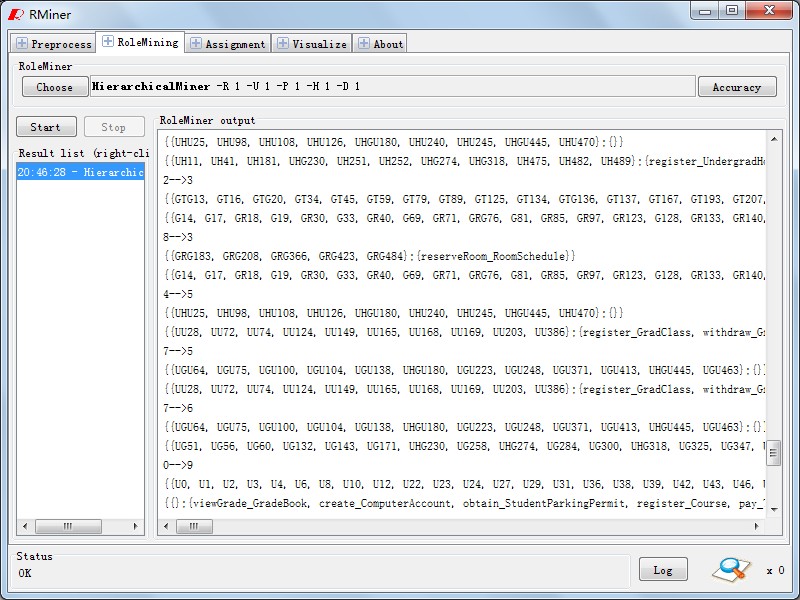
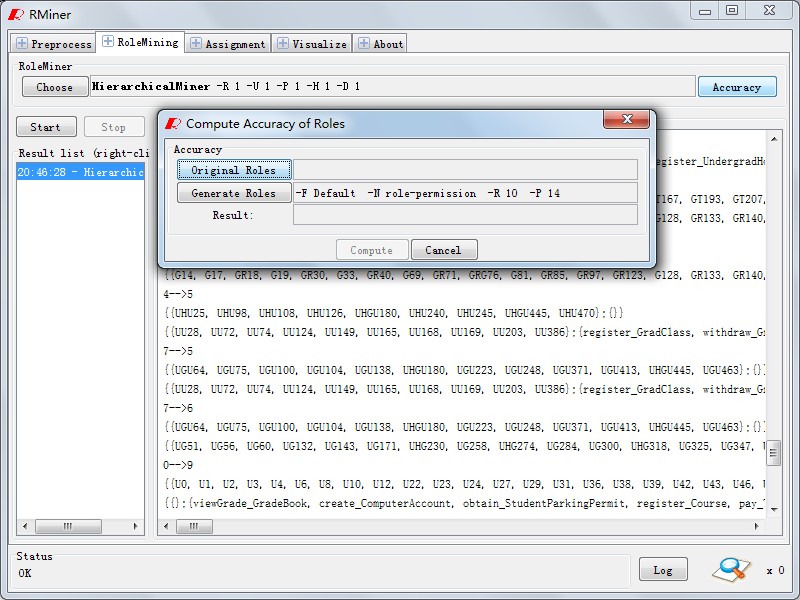
In Panel "RoleMining",as Fig6 ,the process of role mining will be finished. Fig7 shows role mining algrothims we have been implemented,and button"choose" will list them. Similar to WEKA, the algrothim arguments can be configured as Fig8.According to algorithm and configuration, We will output the results in Fig9 after runing it by clicking "start" button. Based on it , button "Accuracy" can be used to analysis the role state accuracy which is similar to Fig10.
|
Fig6. RoleMiner |
Fig7. RoleMiner Algorithm Select |
|
Fig8. Algroithm Arguments Configuration |
Fig9. Results |
|
Fig10. Role State Accuracy |
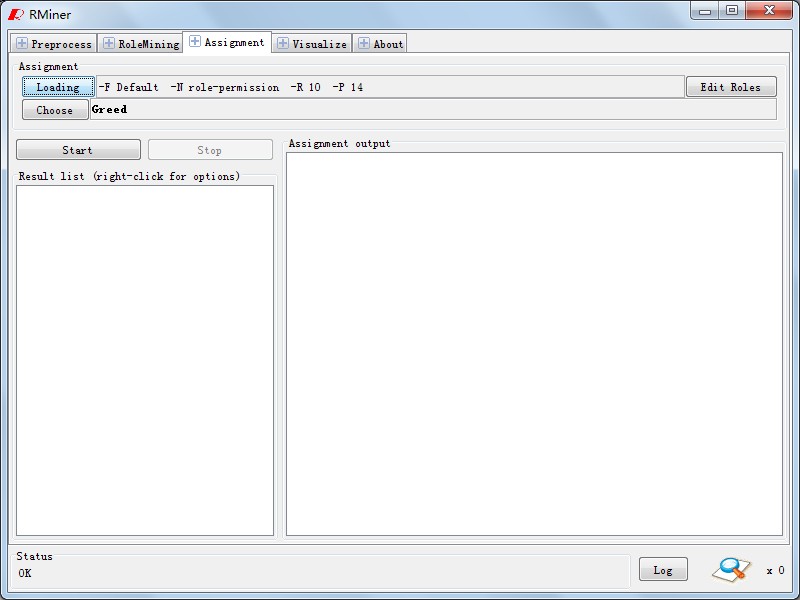
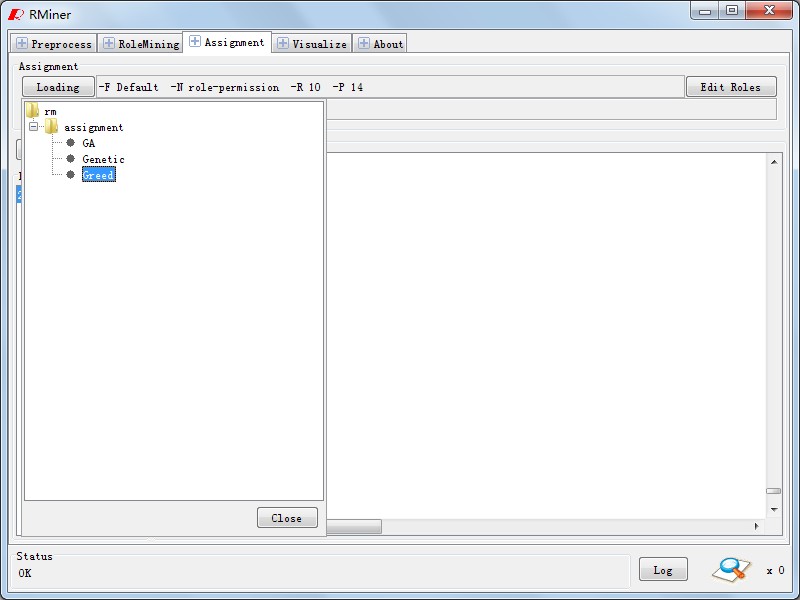
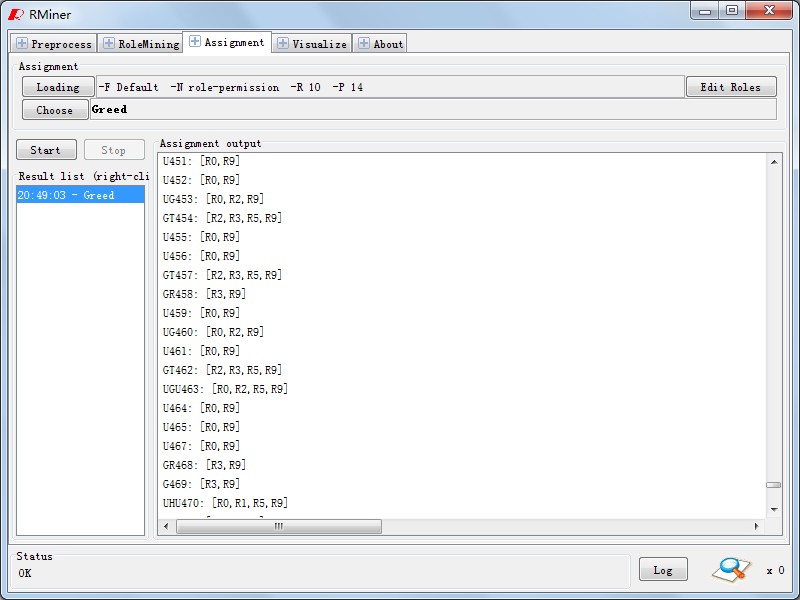
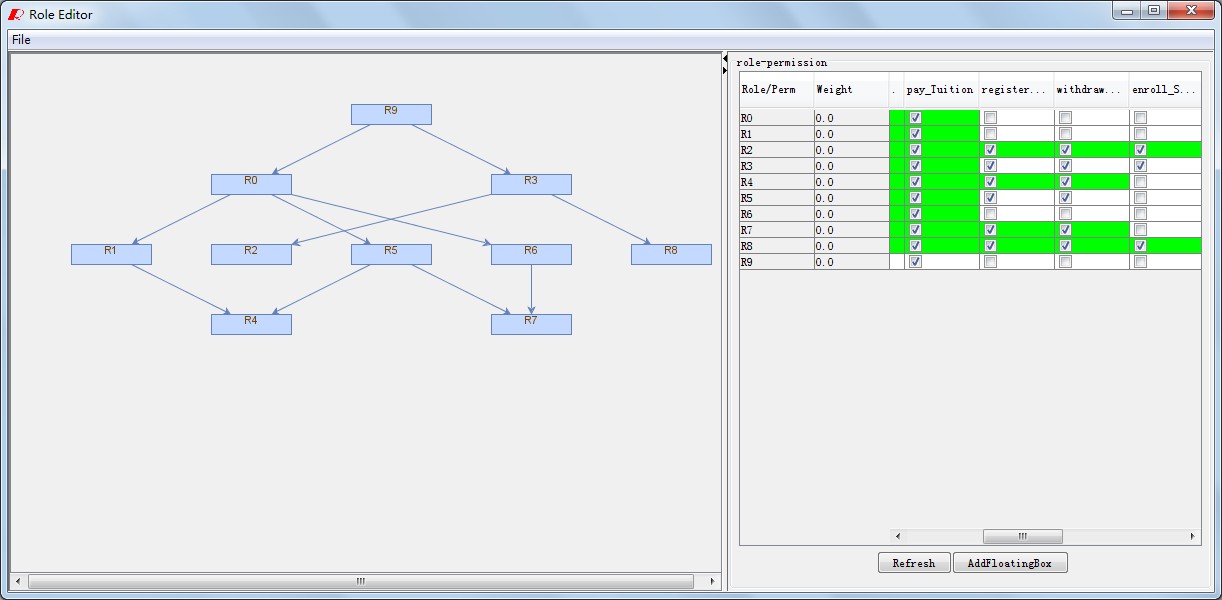
The role assignment function is implemented in panel"Role Assignment" as Fig11. In Fig12,three role assignment algorithm is listed in current. You can choose anyone to do this and will get the results likely Fig13. Of course, if these outputs are not satisfied with users security need, user can update them by a visualization tool, role editor, as shown in Fig14.
|
Fig11. Role Assignment |
Fig12. Role Assignment Algorithm |
Fig13. Results of Role Assignment |
Fig14. Role State Assignment |
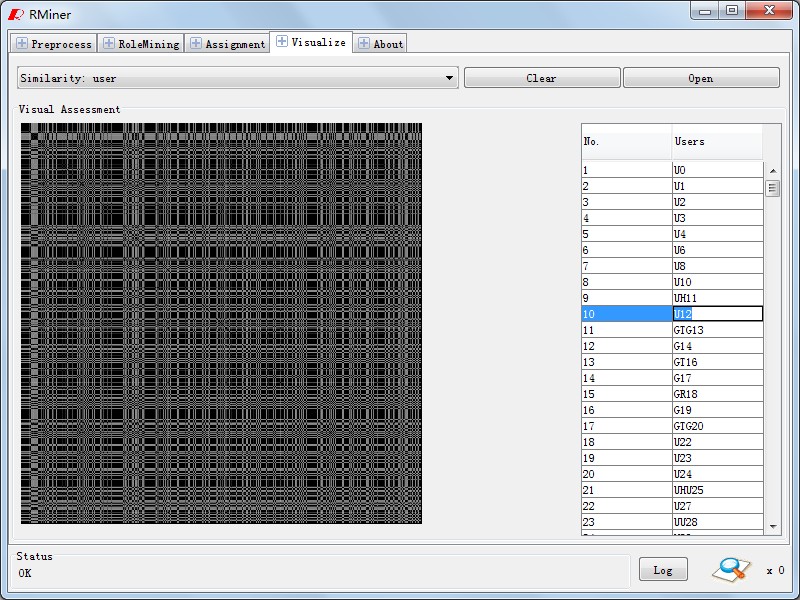
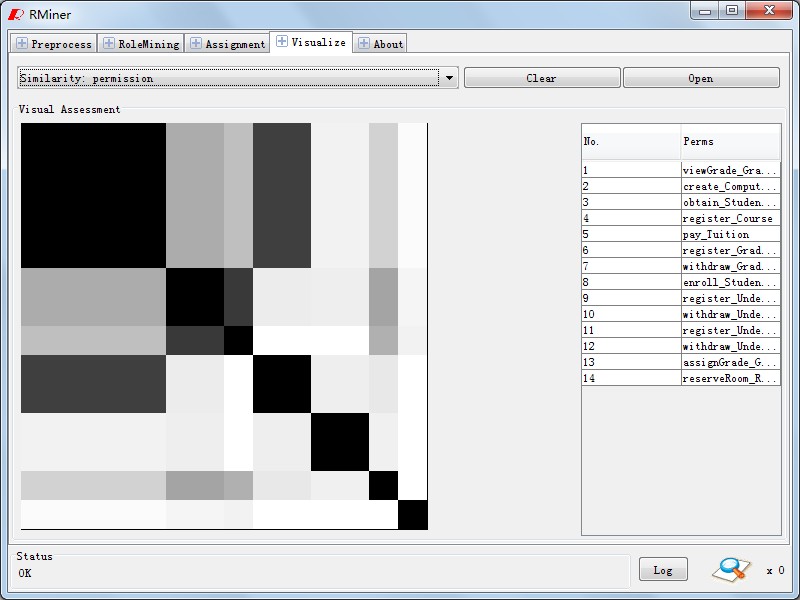
After loading the role to permission assignment relationship and the attributes of the subject and object, you can see these attribute information and assignment relationship information through the visualization module of RMiner. Through the module, you can also know the similarity information of the users and the permissions in the user to permission relationship table. As shown in Fig15, the information is outputed via scatter plot, histogram or line chart. Through the permission similarity information showed on the interface, we can estimate the number of the roles initially accroding to Fig16. We needn’t run role mining algorithm and we can also know the number of the roles roughly, especially, when the role mining algorithm need spend much time but we just need know the number of the roles roughly.In the five modules, the log module records the other modules information which contains exception information, status information, time information and space information, we do not list it here since you can read it in tool.
Fig15. User Similar Statistics |
Fig16. Permission Similar Statistics |
Developers
Prof. Ruixuan Li : /hust/mu_idc/rxli/
Master. Wei Wang : ybwei.wang@smail.hust.edu.cn
Master. Huaqing Li : lihuaqing514439@126.com
ph.D. Xiaopu Ma : xpma@smail.hust.edu.cn
ph.D. Wei Ye : csio@hust.edu.cn
References
[1] Ruixuan Li, Huaqing Li, Wei Wang, Xiaopu Ma, Xiwu Gu. RMiner: A Tool Set for Role Mining. The 18th ACM Symposium on Access Control Models and Technologies (SACMAT 2013), Amsterdam, Netherlands, Jun 12-14, 2013
[2] Xiaopu Ma, Ruixuan Li, Zhengding Lu. Role Mining Based on Weights. The 15th ACM Symposium on Access Control Models and Technologies (SACMAT 2010), Pittsburgh, PA, USA, June 9-11, 2010, pp. 65-74
[3] Jinwei Hu, Yan Zhang, Ruixuan Li, Zhengding Lu. Role Updating for Assignments. The 15th ACM Symposium on Access Control Models and Technologies (SACMAT 2010), Pittsburgh, PA, USA, June 9-11, 2010, pp. 89-98
[4] Xiaopu Ma, Ruixuan Li, Zhengding Lu, Wei Wang. Mining Constraints in Role-Based Access Control. Mathematical and Computer Modelling, Elsevier, 2012, 55(1-2): 87-96
[5] Ruixuan Li, Wei Wang, Xiaopu Ma, Xiwu Gu, Kunmei Wen. Mining Roles using Attributes of Permissions. International Journal of Innovative Computing, Information and Control, 2012, 8(11): 7909-7924
Copyright © 2013 Intelligient and Distributed Computing Laboratory
Huazhong University of Science and Technology, WuHan,China